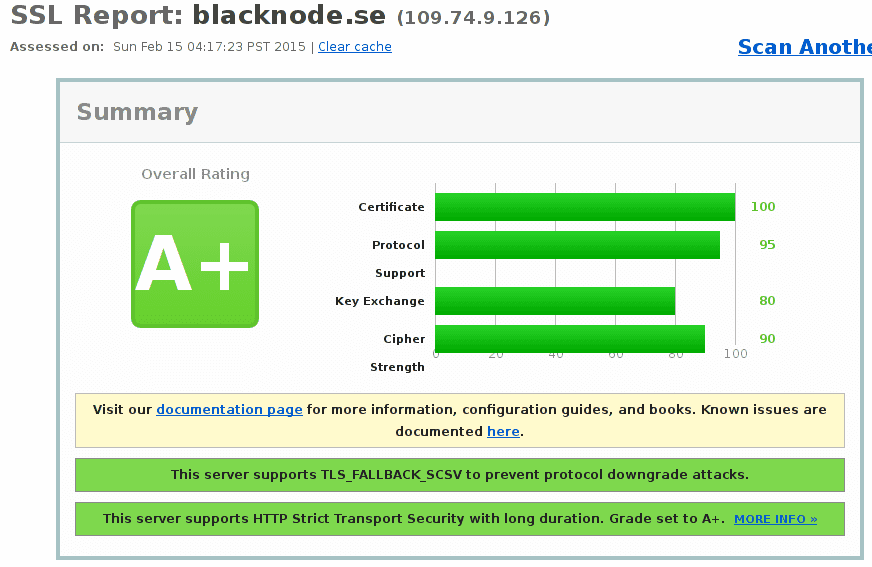
Here are the virtualhost configuration I use to set up https on apache for a site. Today is the 2015-02-24 and this configuration currently achieves an A+ grade on the Qualys SSL Test if you have a trusted certificate.
I’m using my own invoicing project as an example here. In my previous post I created its cert and signed it using my CA.
First off, we need a virtual host which answers on port 80. All this will do is redirect to the https service.
<VirtualHost *:80>
ServerName faktura.blacknode.se
ServerAlias faktura.blacknode.se
Redirect 301 / https://faktura.blacknode.se
</VirtualHost>Now to the more interesting configuration on the https port.
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerAdmin webmaster@blacknode.se
ServerName faktura.blacknode.se
ServerAlias faktura.blacknode.se
WSGIScriptAlias / /usr/local/lib/faktura.blacknode.se/faktura.wsgi
<Directory /usr/local/lib/faktura.blacknode.se>
Order deny,allow
Allow from all
</Directory>
# Possible values include: debug, info, notice, warn, error, crit,
# alert, emerg.
LogLevel warn
ErrorLog ${APACHE_LOG_DIR}/faktura.error.log
CustomLog ${APACHE_LOG_DIR}/faktura.access.log combined
# SSLstuff
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA RSA+3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS"
SSLCertificateFile /etc/ssl/certs/faktura.signed.crt
SSLCertificateKeyFile /etc/ssl/private/faktura.pem
SSLCertificateChainFile /etc/ssl/certs/blacknode.dev.signed.crt
Header set Strict-Transport-Security max-age=15552000
</VirtualHost>
</IfModule>Pay attention to the SSL directives.
SSLProtocol all -SSLv2 -SSLv3This disables SSLv2 and SSLv3, which are unsafe, but still allows TLS.SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 ..."These are a set of currently secure ciphers which we explicitly allow and not allow. I believe I got these from the documentation at Qualys. Insecure ciphers, like e.g. RC4 are discarded.SSLCertificateFile /etc/ssl/certs/faktura.signed.crtThe path to my public certificate.SSLCertificateKeyFile /etc/ssl/private/faktura.pemThe path to my private key.SSLCertificateChainFile /etc/ssl/certs/blacknode.dev.signed.crtThe path to my intermediate CA. The clients need this to help validate up to the root CA, which you have installed.Header set Strict-Transport-Security max-age=15552000Sets the Strict-Transport-Security header, telling your browser that it should only connect via https in the near future (half a year or so). It will internally redirect any attempts to connect to http.
Anyway, that’s my apache confs as of current. Maybe you will find some use for them. If you have any suggestions on how to improve it further, don’t hesitate to contact me!