It’s Sunday and I wanted to play some computer games to relax before the next work week. I’m a quite happy customer of Shadow, which is a gaming VM in the cloud that I’ve been using for the past months. Basically it’s a windows VM with very good gaming hardware that you rent access to.
However this Sunday I was faced with an issue. So I tried and successfully managed to hack my way around it.
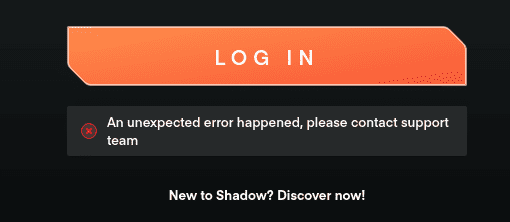
When trying to login, it simply gives me an error:
I try to login via the website, which works fine. So my password is still fine. I decide to investigate.
I boot up wireshark to try to figure out what Shadow does happening when the client tries to log in. I start a capture
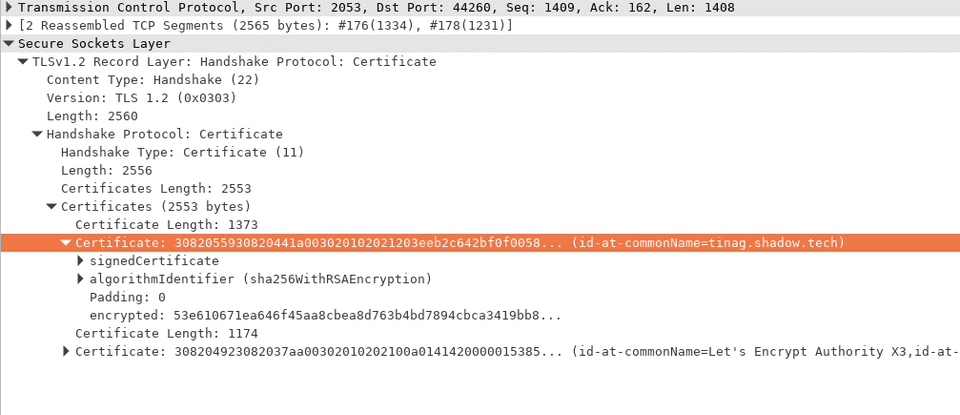
and try to log in. In the capture I find the following SSL connection, where I see the client is trying to
connect to the tinag.shadow.tech domain on port 2053.
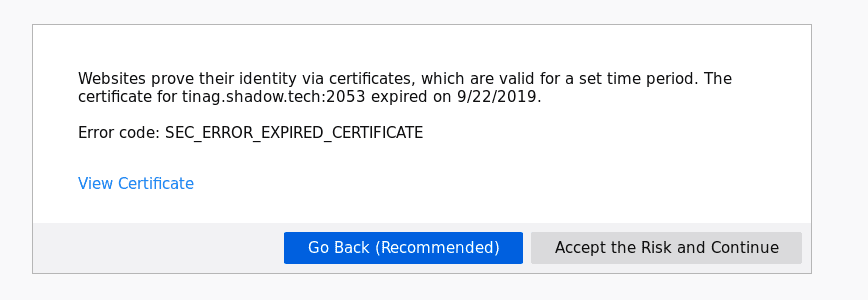
I decide to check out the website in my browser, because it’s probably a web api. Connecting to the https://tinag.shadow.tech:2053 I get the following certificate error:
So the certificate had expired. Probably Shadow team had simply forgotten to renew it (protip: set up monitoring on this). I sent some messages on Discord, Twitter and via the support and decided to wait.
Then I got bored of waiting.
After some trial and error, I instead managed to get the shadow client to communicate with the server through a reverse proxy.
I installed mitmproxy, and ran the following command to start a reverse proxy accepting SSL/TLS connections on port 2053.
mitmproxy -p 2053 --ssl-insecure --mode reverse:https://85.190.64.32:2053/Then I add 127.0.0.1 tinag.shadow.tech to my /etc/hosts file.
Next I need to get the Shadow client to trust my mitmproxy’s certificate. After some digging I find that the client is using electron. By passing the NODE_TLS_REJECT_UNAUTHORIZED environment variable I’m able to tell the client to ignore certificate errors.
NODE_TLS_REJECT_UNAUTHORIZED=0 ./opt/Shadow/shadowAnd look, it works 🎉! I’m also able to access the VM now.
Yes I’m aware this means technically my ISP or any host inbetween my client and shadow’s server could MITM my connection, but I’m not concerned about anything sensitive running on this server, my password is unique, and this is just temporary until Shadow’s team is able to renew the certificate.