Url Secrets
Found a neat little hack using “World Wide Web URLs”
A reference to a particular part of a document may, including the fragment identifier, look like
http://www.myu.edu/org/admin/people#andy
in which case the string "#andy" is not sent to the server, but is retained by the client and used when the whole object had been retrieved.This gave me an idea of using the “fragment identifier”, aka what’s behind the #, to send secrets which can be seen by other browsers, but not the server. Secrets like for example passphrases which can be used for cryptographic purposes.
I made a small proof of concept project using this idea for a service to share secret message. Using clientside crypto, the user can submit an encrypted message to the server. The server returns with a uuid to identify the message. The client side script then creates a url containing the uuid and encryption key. Like so:
http://domain.tld/[uuid]#encryptionkeyThe user sends this url to his friend. When the friend opens the url, the server sends back the encrypted message. The client side script grabs the encryption key and decrypts the message. The plaintext message is never seen by the server.
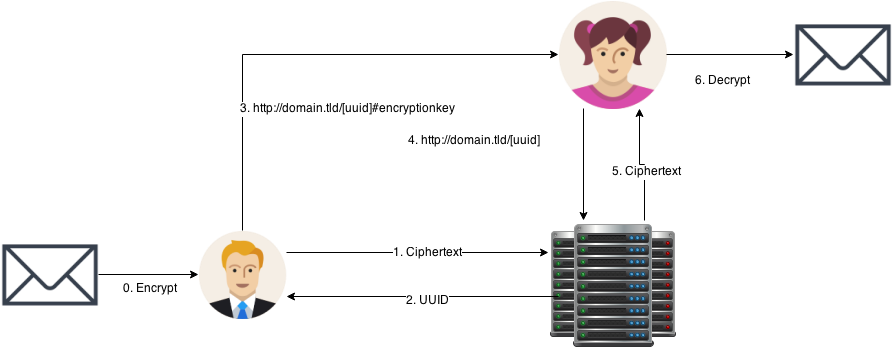
You can find a demo here (note unsigned https) and the github repo here.
Obviously, this idea implies trusting the clientside script that is sent by the server. If the server was adversarial he could easily modify the script to remove the encryption or send the encryption key to the server.